About InsecureShop
InsecureShop is an intentionally designed vulnerable Android application built in Kotlin.
The aim of creating this application is to teach developers and security professionals about the vulnerabilities present in modern Android applications. This also serves as a platform to test your Android pentesting skills.
The InsecureShop project was released as part of the SourceZeroCon 2021 (Slides | Video).
You can checkout the project here: https://www.insecureshopapp.com
Research
In early 2020, I started my research on Android WebView and how loading an untrusted URL in applications’ WebView can lead to the exfiltration of session cookies and local storage files by leveraging symlink attacks and insecure WebView properties. As part of the research, more than 100 popular Android applications were analyzed. The majority of the applications were running vulnerability disclosure programs on Hackerone, Bugcrowd and Synack. Some of the applications were the ones that had more than 100 million downloads in the Google play store.
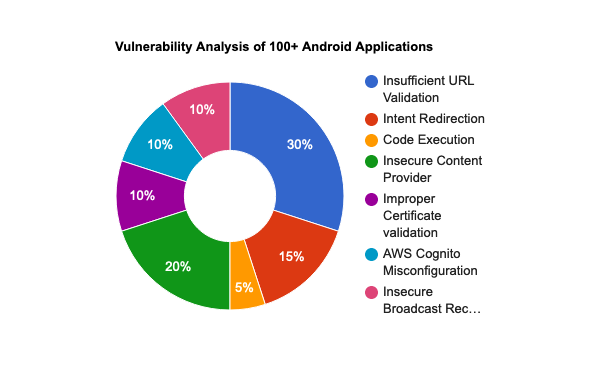
The majority of the issues (30%) account for the insufficient URL/Host validation, which allowed remote attackers or third-party applications on the device to load arbitrary websites or content within the WebView.
The 20% of applications suffered from misconfigurations in the Content Provider, which allowed third-party applications on the device to steal sensitive data. In some cases, it was possible to perform SQL Injection due to a vulnerability in the projection field of the Content Provider.
The 15% of applications were found vulnerable to Intent Redirection, which allowed third-party applications on the device to call any non-exported IPC components.
The following chart gives a rough snapshot of the vulnerabilities identified.
Vulnerabilities
Most of the vulnerabilities found during the analysis of Android applications are added within the Insecureshop app.
Insecureshop v1.0 contains the following vulnerabilities:
- Hardcoded Credentials
- Insufficient URL Validation
- Weak Host Validation
- Arbitrary Code Execution
- Intent Redirection
- Unprotected Data URI
- Theft of Arbitrary files from LocalStorage
- Using Components with Known Vulnerabilities
- Insecure Broadcast Receiver
- AWS Cognito Misconfiguration
- Insecure use of FilePaths in FileProvider
- Use of Implicit Intent to send a broadcast with sensitive data
- Intercepting Implicit Intent to load Abitrary URL
- Insecure Implementation of SetResult in expoted activity
- Insecure Content Provider
- Lack of SSL Certificate Validation
- Insecure WebView Properties Enabled
- Insecure Data Storage
- Insecure Logging
Check out the challenge page here: https://docs.insecureshopapp.com/. This space is only intended to point out the vulnerabilities implemented in the InsecureShop app and the vulnerable code used. This space won’t provide you with complete solutions for all the vulnerabilities that are implemented in the InsecureShop app. However, this will definitely give you nudge in the right path.
Future Work
- Upcoming releases with more features and vulnerabilities (Planned to launch v2 in 2024).
- A patched version of InsecureShop application highlighting best coding practices.
